Technically every attempt to define or describe blockchain technology - its features and mode of operation cannot do without the use of terms (e.g. authenticity, auditability, unchangeability, indestructibility, non-repudiation), which are also used to describe the issue of information security management. Already this statement indicates that the blockchain has several information security (IBs) contact points.
In this subchapter, we focused on analyzing these contexts, advantages and disadvantages of blockchain in terms of information security management and indicating the use cases in which the blockchain may contribute to increasing the security of the information assets in question.
Objectives and procedures of information security management
At the beginning, we offer a brief reminder of the basic concepts and concepts of information security.
Information security can be defined as the state when there are in relation to protected information all requirements met in relation to security. For the purposes of IB (also known as the CIA) is to ensure sufficient:
• confidentiality,
• integrity a
• the availability of these information assets.
Note: For the purposes of this document, the term integrity will also mean the so-called undeniability (non-repudiation) of origin - sending of data and undeniable receipt of data but also authenticity of data - the ability to verify who the author of the data is, when it was created and that it has not been altered.
Under information security management, we then understand the implementation of activities that are aimed at achieving mentioned objectives of the IB. These activities consist in the periodic implementation of the following steps:
• identification and modeling of information assets and their context,
• risk analysis, i. identification and quantification of threats, vulnerabilities and potential (negative) impacts acting on these assets and the calculation of the so-called inherent risks,
• selection and implementation of appropriate ("sufficiently strong") control mechanisms (hereinafter also "KM") on mitigation of inherent risks to an acceptable level (according to the chosen risk acceptance strategy) and calculation of the so-called residual risks,
• testing (design and effectiveness) of implemented information security control mechanisms (i.e. confirming that KM fulfills its role and really reduces risks to an acceptable level), axle - KM improvement,
• monitoring, identifying and resolving information security incidents (i.e. situations where it could despite the implemented KM, be a negative impact on a certain information asset, which caused by a certain threat and exploiting a certain vulnerability of that asset).
The following image is a simplified illustration of part of information management security related to risk analysis.
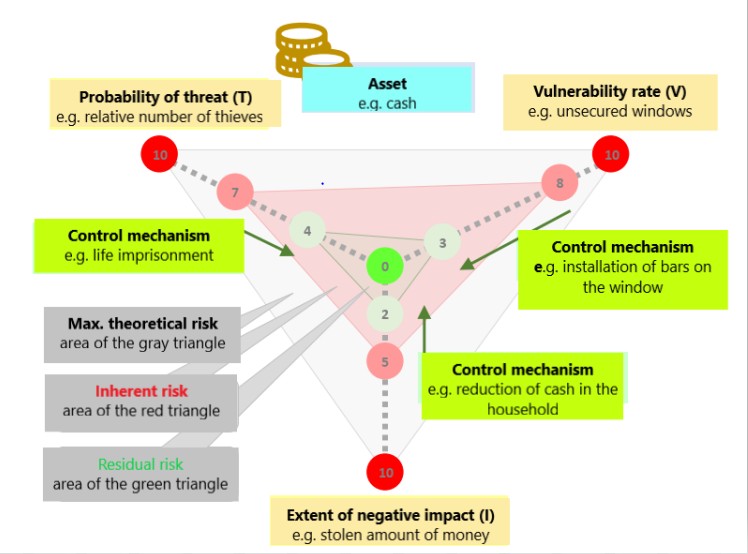
Example of risk calculation for an information asset
Information security management in public administration
The basic generally accepted guide for information security management is a set of standards ISO 27000, which follows the original series of British standards BS 7799 (this applies at least to European area and e.g. The US follows standards issued by NIST).
Effectively all European and national strategies and legislation in relation to information (and cyber) security are based on this set of standards.
Requirements for information security for ISVS are documented in the Decree of the Ministry of Finance of the Slovak Republic on standards for Public administration information systems[1] - Security standards covering the following areas:
• Standards for management architecture (§ 29 - § 32),
• Minimum technical security standards (§ 33 - § 44).
It is clear that data security and system functionality is a very important prerequisite for success transformation from "paper" to digital public administration. At the moment, what resonates hugely in society in particular is the need to protect personal data (GDPR Regulation - see also section 3.4.1) as well as threats of so-called cyber security (which is a subset of the broader concept of information security), to which Act no. 69/2018 Coll. on Cyber Security[2] and are also covered by Act 45/2011 Coll. on critical infrastructure[3].
Information security in blockchain
This section provides an insight into the role of blockchain technology in managing information security – its advantages and disadvantages compared to traditional (centralized) solutions but also its vulnerabilities, which typically are not proprietary to centralized solutions and in the case of emerging distributed applications based on blockchain will need to be further explored in detail, tested and monitored as their methods evolve abuse.
Notes:
• For the purpose of analyzing the potential of IB control mechanisms implemented in blockchain technology we will understand information assets mainly as information assets of the data type (data – representing values of modeled reality quantities) but also data representing source codes of programs (smart contracts) processing these data.
• The term data may also include metadata on other types of information assets (e.g. on information services, hardware, software, network elements, ICT-containing spaces, etc.).
Blockchain technology control mechanisms
As already mentioned in the introductory paragraph of subchapter 3 in the discussions on blockchain technology, they often inflect terms from the information security dictionary. This is due to the fact that this technology implicitly contains several modern and very effective IB control mechanisms that are necessary for the blockchain to fulfill the basic task for which it was developed - the creation of a reliable and a credible (distributed and decentralized) communication environment between different "Types" of participants (participants from different entities who do not potentially trust each other) without having to organize such communication system, managed and supervised for that purpose by central authority.
In the context of the "triangle" of the information risk calculation (Image 7), the control mechanisms of blockchain focuses on reducing inherent risk by reducing vulnerability information assets of the "data" type (see notes in the introductory paragraph of this subchapter). These default KM blockchain has no ambition to reduce the likelihood of a threat or a negative impact on information assets - these are external, uncontrollable factors in terms of blockchain technology.
KM blockchain protects data "only" against some types of threats, but they can reduce data vulnerabilities significantly. These are vulnerabilities to threats in failure to meet the basic objectives of IB, in:
• data unavailability,
• loss or destruction of data,
• intentional or accidental modification of data,
• denial of sending or receiving data,
• non-delivery, repetition (duplication), synchronization of messages or transactions and partly also
• entering false data and unauthorized access to sensitive data.
The control mechanisms that blockchain technology provides to "its" distributed applications are generally of a different nature than common (traditional) applications and information systems. The basic comparison of KM is given in the following table.
Notes:
• The KM classification used is intended to emphasize the differences between blockchain and traditional solutions, it is not complete in terms of information security theory.
• Since blockchain technology is used to record only relatively simple data sentences (transactions, messages, events or regulations for their processing) it can happen that its comparison with traditional information systems (in management of IB), which often use very extensive and complicated databases, that the comparison will seem unfair. Therefore, it is necessary to properly "calibrate" expectations and see the traditional solution rather than a relatively simple centralized application with a simple database but allowing remote access to many users in multiple roles.

